Ethical Hacking
Feminist IT 2 the Sky!
27th September 2025, Wien
This is the waiting queue slide. Hit space or right arrow key to jump to cover slide.
Ethical Hacking
hack & learn day ☆ 27th September 2025 ☆ TU Wien

jackie / Andrea Ida Malkah Klaura <jackie@tantemalkah.at>
https://tantemalkah.at/2025/fits-hacking
 All contents, unless otherwise noted, were produced by Andrea Ida Malkah Klaura
All contents, unless otherwise noted, were produced by Andrea Ida Malkah Klauraunder a Creative Commons Attribution - Share Alike 4.0 International License.
The feminist technoscience logo on the waiting queue slide is an adaptation of a public domain image.
🌒⇆🌖 Use page style to switch to light mode.
Outline
- Intro me & ethical hacking
- Security basics
- Intro web app sec
- practical hacking: XSS
- Interlude: VMs & Docker containers
- 🍲 🌮 🥪 lunch break 🥪 🌮 🍲 (13:00-14:00)
- more hacking: SQLi, Command injection, file inclusion
And whoami?

- IRL: jackie
- officially: Andrea Ida Malkah Klaura
- part of the base dev team @Angewandte since 2020
- also here at TU Wien and some other unis
- activist for better tech for everyone
- #morefunnotprofit
- Never Trust A Running System!
- more info on tantemalkah.at
pronouns
- in binary gender space: she/her
- in the wider gender multiverse: ze/hir
- usage: https://my.geeky.gay/pronouns/ze/hir/hirs/hirself
That gender you got at birth? That's just a tutorial gender. You're only supposed to use it to get the hang on this world's gender system and then ditch it for a stronger one, not use it your entire life, noob
And what are we hacking these days?
- ditact: Hack the heck out of this website!
- FH Salzburg: Ethical Hacking
- TU Wien: Feministische Technikforschung
- feminist linux meetup
- and a few more other things
What is ethical hacking?
"A white hat (or a white-hat hacker, a whitehat) is an ethical security hacker. Ethical hacking is a term meant to imply a broader category than just penetration testing. Under the owner's consent, white-hat hackers aim to identify any vulnerabilities or security issues the current system has. The white hat is contrasted with the black hat, a malicious hacker; [...] There is a third kind of hacker known as a grey hat who hacks with good intentions but at times without permission."
Wikpedia [en]: White hat (computer security)
"The purpose [...] is to provide individuals the information once held only by governments and a few black hat hackers. In this day and age, individuals stand in the breach of cyberwar, not only against black hat hackers, but sometimes against governments. If you find yourself in this position, either alone or as a defender of your organization, we want you to be equipped with as much knowledge of the attacker as possible.
To that end, we submit to you the mindset of the gray hat hacker, an ethical hacker that uses offensive techniques for defensive purposes. The ethical hacker always respects laws and the rights of others, but believes the adversary may be beat to the punch by testing oneself first."
Harper et al. 2018: Gray hat hacking: the ethical hacker's handbook. p. xxix
Vulnerability Assessment vs Pentest
- Vuln. assessements are usually just scans (and also part of pentests)
- Can be automated and conducted very regularly
- Pentests require expertise an manual effort (in addition to automated tools)
- Depending on scope...
- vuln. scans take a few minutes to hours
- pentests take a few days to weeks
- Recommended (but depending on size and type of organisation & IT dept.):
- Vuln. scans: weekly to quarterly
- Pentests: quarterly to yearly
- and both in case of significant system changes
Standards?
There is no standard!
- But a few good frameworks
- OWASP Web Security Testing Guide (OWASP, Open Web Application Security Project)
- Open Source Security Testing Methodology Manual (ISECOM, Institute for Security and Open Methodologies)
- Technical Guide to Information Security Testing and Assessment (NIST, National Insitute of Standards and Technology)
- Penetration Testing Guidance (PCI SSC, Payment Card Industry Security Standards Council)
- and many more, like PTES (a very practical wiki guide, no HTTPS though!)
Pentest Lifecycle
- Pre-engagement phase
define the scope! - Intelligence gathering
- Vulnerability analysis
- Exploitation
- Post-exploitation phase
- Reporting
Scope & Rules of Engagement important!
- It is dangerous to go alone!
- It is much more dangerous to go without rules of engagement!
- Most of the things we do in ethical hacking would be illegal in most jurisdictions, without the consent of the hacked person
- And from a feminist perspective: hacking someone with out consent is really not a thing we want to do
- There is this gray area of the hack-back(technically still illegal)
- Always get permission in writing!
- With proper definition of the scope and rules of engagement!
Intelligence gathering
- Most important part during an engagement
- Ground rule: the more and the more detailed the gatherd infos, the more attack vectors we have in later stages
- But: Rules of Engagement set limits on what infos we can gather
- OSINT (Open Source Intelligence) is always possible
- In black box tests OSINT is the only means of up-front info gathering
passive vs active recon (reconnoissance but cooler)
- passive:
- we only use freely available info, without direct interaction of any target systems
- collect info about the target but not from the target
- no data transfer to target organisation (also not the website)
- semi-passive:
- includes everything that looks like normal system usage
- e.g. browse the target organisation's website, etc.
- active:
- we alse use (technical) sources (in scope), which are publically accessible
- e.g. port scanning, fingerprinting, publically accessible test systems, etc.
- can potentially be recognised as suspicious activity by target org
vulnerability analysis
- extends recon/info gathering
- not gathering more infos about the target
- but actively searching for vulnerabilites
- e.g. with automated scans (not only port scan, also checking if service is vulnerable)
- e.g. for web apps found in recon, we test if they have any vulns
- we actively try to find hidden artefacts, e.g. with directory enumeration
- there is also passive vuln. analysis, based on meta data analysis or traffic monitoring
Exploitation
- now we use all the found vulnerabilities
- we need to assume there will be counter-measures
- not all vulnerabilites are valuabale, but all have to be tested (if in scope) and documented
- also found counter-measures have to be analysed and documented
- in the end we always want to provide suggestions for improvements and recommendations on how to close vulnerabilities
- this stage can be trained especially in CTFs (Capture The Flag tournamets) or other training scenarios (like this workshop)
- caveat: takes time, we can only do so much in a day, but we have a very vulnerable web app at hand, so we get to exploit at least a little bit
Disclaimer
This was just an excerpt of the most essential things you need to know about ethical hacking or pentesting. There is so much more, especially the reporting phase is crucial. But exploitation is probably most fun, so let's go for it.
One more caveat: you need some security basics and know a little bit about web applications first.
some security basics

(Source: https://xkcd.com/538/ , under CC BY-NC 2.5 license)
Terminology
the CIA triad
- macro level key goals in Information Security
- Confidentiality
- a property of an information system that ensures that users can always only get those informations from the system for which they are authorized to read them
- Integrity
- a property of an information system that ensures that data can be changed only by users who are authorized to do so
- Availability
- a property (or the degree thereof) that an information system is providing functions whenever it is supposed to provide those functions
Access Control
- differentiating between different users of an information system
- Identification
- a process of claiming that someone is who they say they are
- e.g. by providing an ID card (IRL), or a username (on the web)
- Authentication
- a process of actually verifying that the identification is valid
- by something you know: e.g. a password or passphrase, a PIN or some other code, an answer to a question, …
- by something you have: e.g. a token, an ID card, an RFID chip, …
- by something you are: e.g. finger print, the scan of your retina, …
- use more than one property (MFA - Multi-Factor-Authentication)
- Authorization
- a process to check whether a specific user is allowed to execute a specific action (e.g. read a document, upload a file, change an existing file, send a message, …)
bad, worse, worst
- Vulnerability
- "A vulnerability is a hole or a weakness in the application, which can be a design flaw or an implementation bug, that allows an attacker to cause harm to the stakeholders of an application." (OWASP: Vulnerabilities)
- Exploit
- "a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to cause unintended or unanticipated behavior" (Wikipedia: Exploit (computer security))
- zero day exploit 👿
- An exploit that is "unknown to everyone but the people that found and developed them" (ibid)
where do vulnerabilities come from?
- faulty/buggy/insecure code
- faulty/insecure use of code
- faulty/insecure/missing systematic approach to application development
faulty/buggy/insecure code
- because developers do not know how to write secure code
- because developers are working under too much pressure to satisfy deadlines and deliver code
faulty/insecure use of code
- because administrators do not know how to secure the service
- because documentation is bad and it is unclear how a clean (and secure) setup looks like
- because everyone likes to throw around with the buzzword label DevOps, but in practice there is no systematically engineered process in place to assure the quality and security of complex application systems (this is why there now is also DevSecOps)
faulty/insecure/missing systematic approach to application development
- no one really cares about security
- management layers are ignorant of the importance of security and do not allocate the appropriate resources
- security is not integrated from the start on (e.g. with a secure development life cylce, short SDLC)
the making of a vulnerability
...just some examples...
- in planning & design desicions:
- trusting the user('s browser)
- using outdated or self-coded encryption algorithms and insecure protocols
- while coding:
- incomplete or missing input validation and output sanitization
- insecure methods and queries to access a database
- parsing user provided files (including configs from admins) without precautions
- hardcoding credentials
- at run-time:
- debugging mode in production systems
Cornerstones to remember:
- There is no "100% secure"!
- tools and processes are available to integrate security from the start
- but they need time, experience, and in consequence also a lot of money
- information security is not a specific state you can reach
- rather a chance/probability that you can increase by appropriate measures
Web App Sec
How does a web server work
- A web server is basically a programme
- that listens on one or more TCP ports (usually 80 and 443)
- waits for requests from web clients
- provides whatever information the client requested if it is available on the server
- client and server talk follows HTTP protocol (HyperText Transfer Protocol)
- nowadays mostly HTTPS, which is HTTP over a TLS-encrypted session
HTTP
- is a plaintext protocol
- you could just use
telneton the command line to speak to a server:![]() (Source: https://commons.wikimedia.org/wiki/File:Http_request_telnet_ubuntu.png , under public domain)
(Source: https://commons.wikimedia.org/wiki/File:Http_request_telnet_ubuntu.png , under public domain)
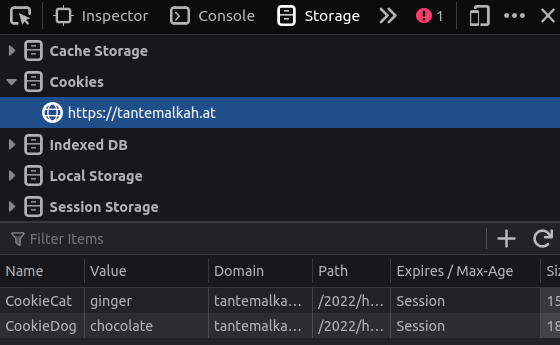
🍪🍪🍪 Cookies 🍪👿🍪
- used for lots of questionable stuff
- but also because HTTP is state-less, e.g. to remember logged in users
-
HTTP responses can contain cookies, e.g.
HTTP/1.1 200 OK Content-type: text/html Set-Cookie: sessionToken=abcdef01234567890; Expires=Tue, 31 Aug 2021 12:34:56 GMT Set-Cookie: foo=bar Set-Cookie: chocolate=good Set-Cookie: raisins=evil -
In the next request to the same site the browser includes those cookies
GET /admin.html HTTP/1.1 Host: www.example.org Cookie: sessionToken=abcdef01234567890; foo=bar; chocolate=good; raisins=evil;
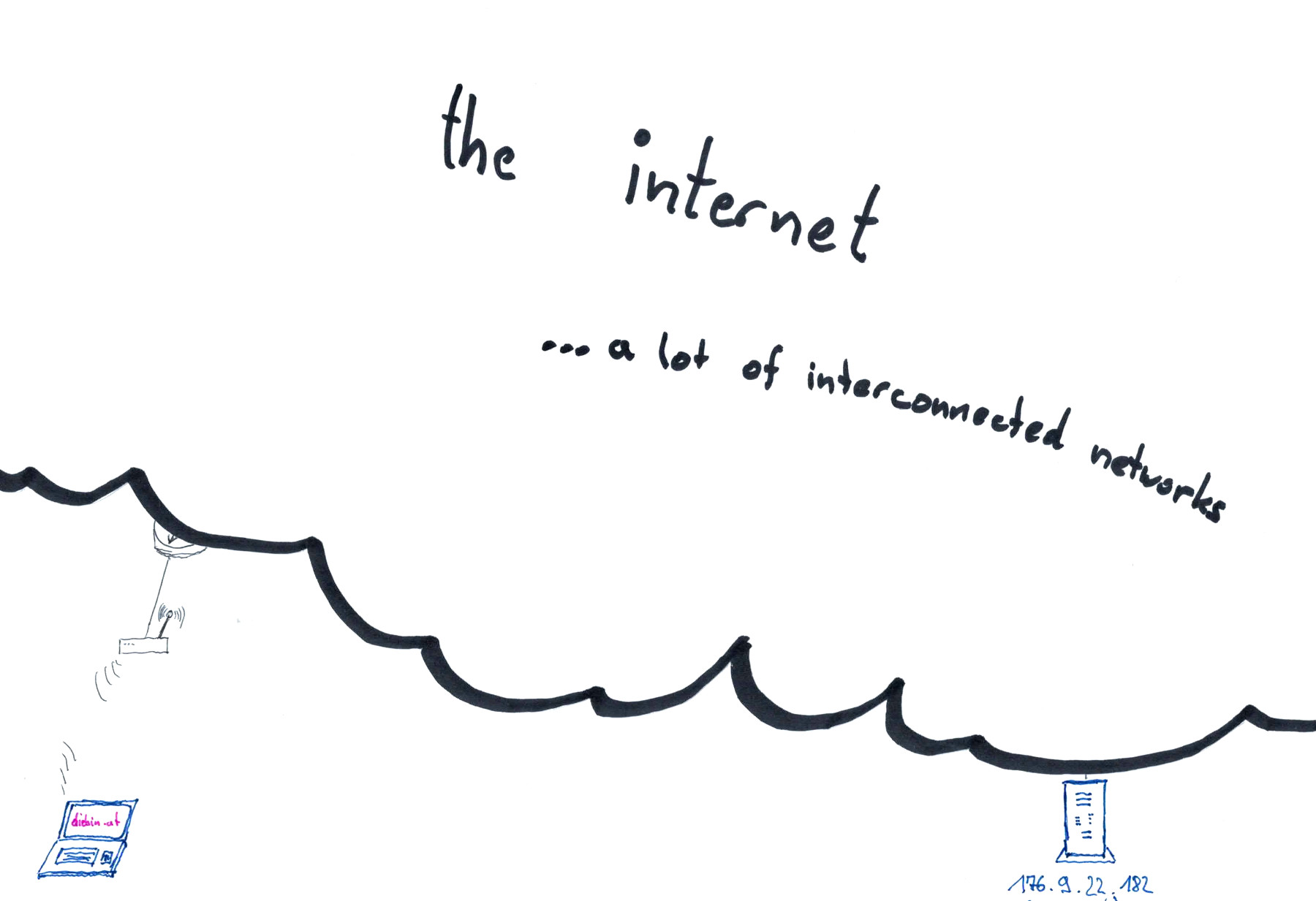
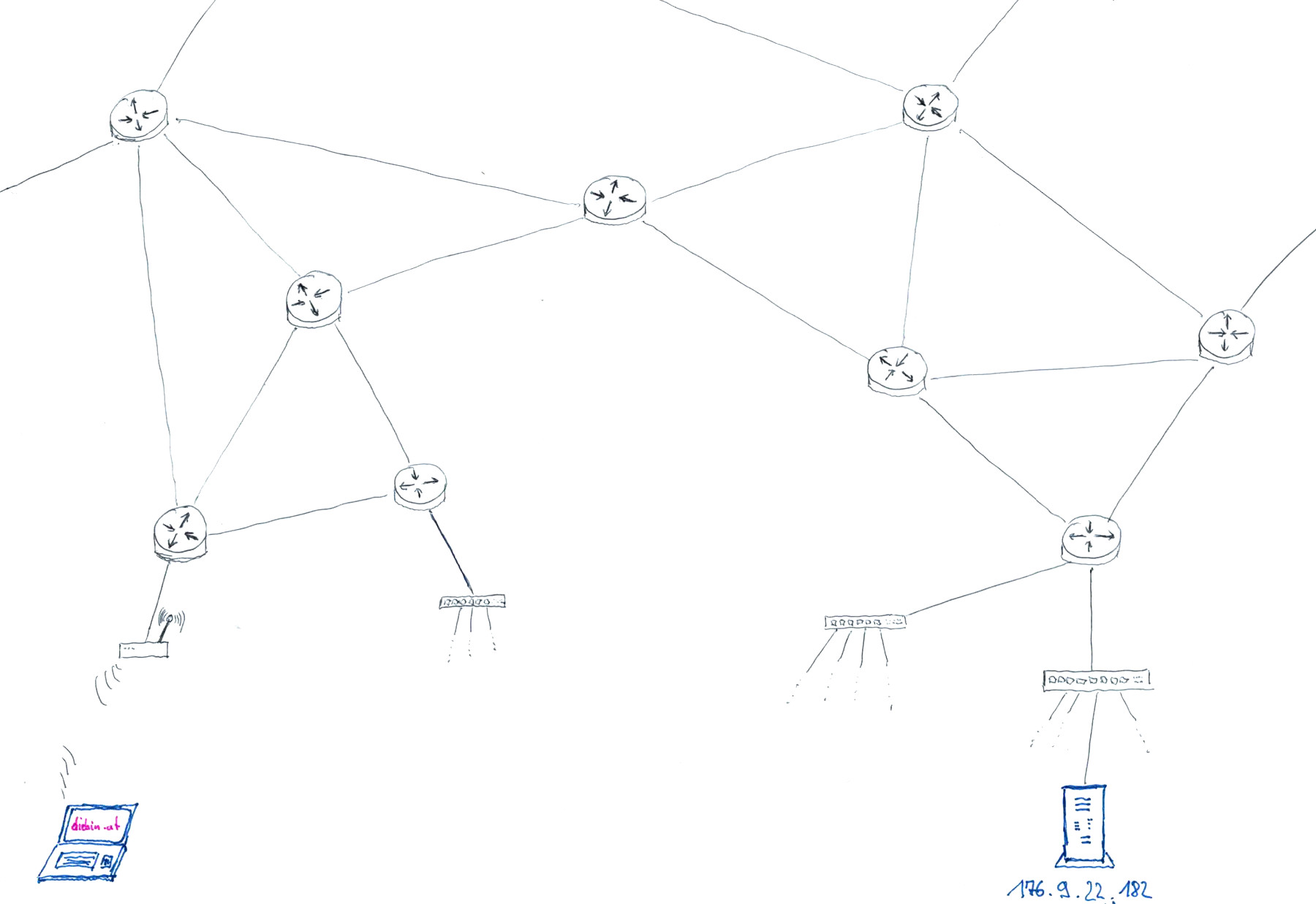
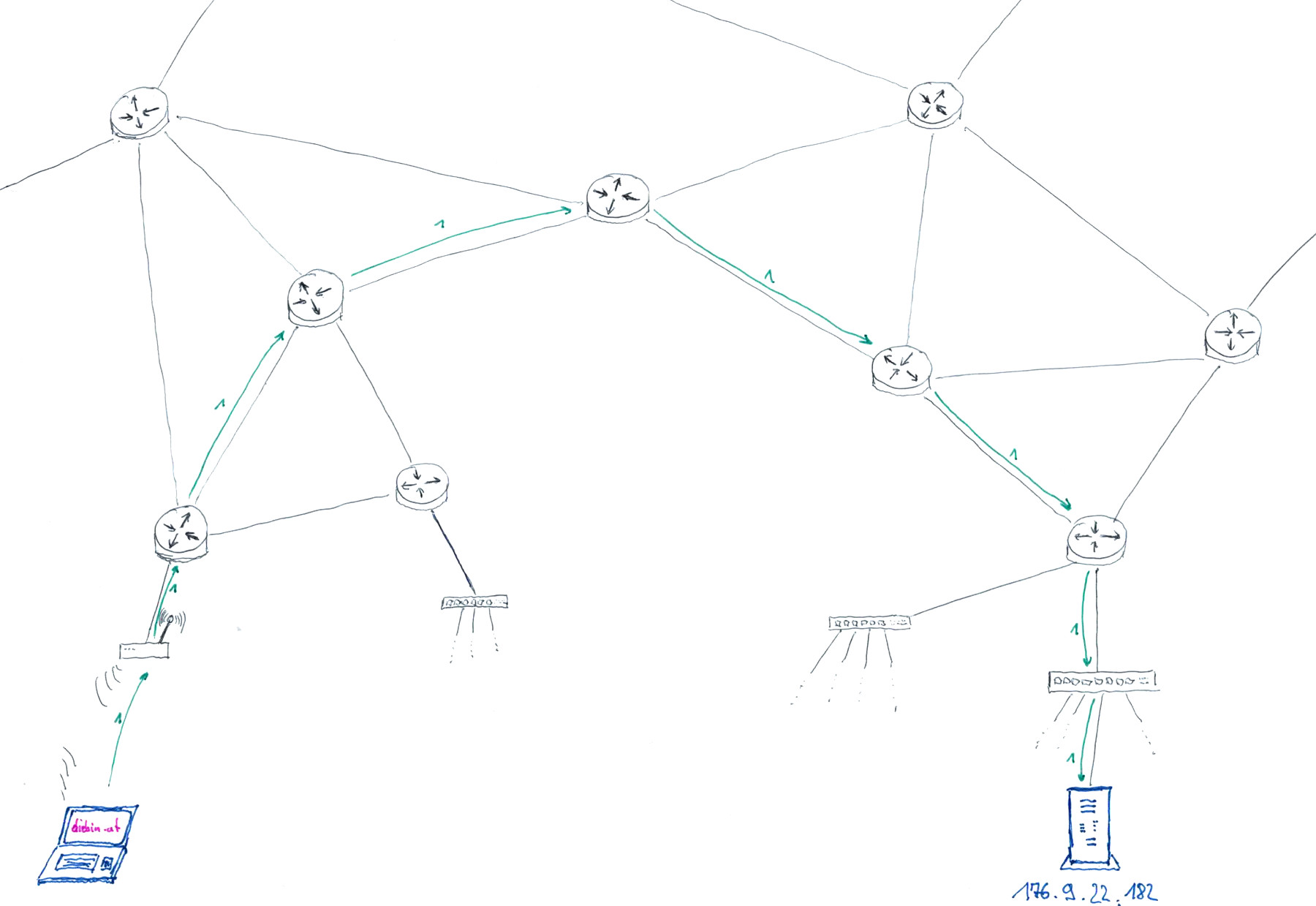
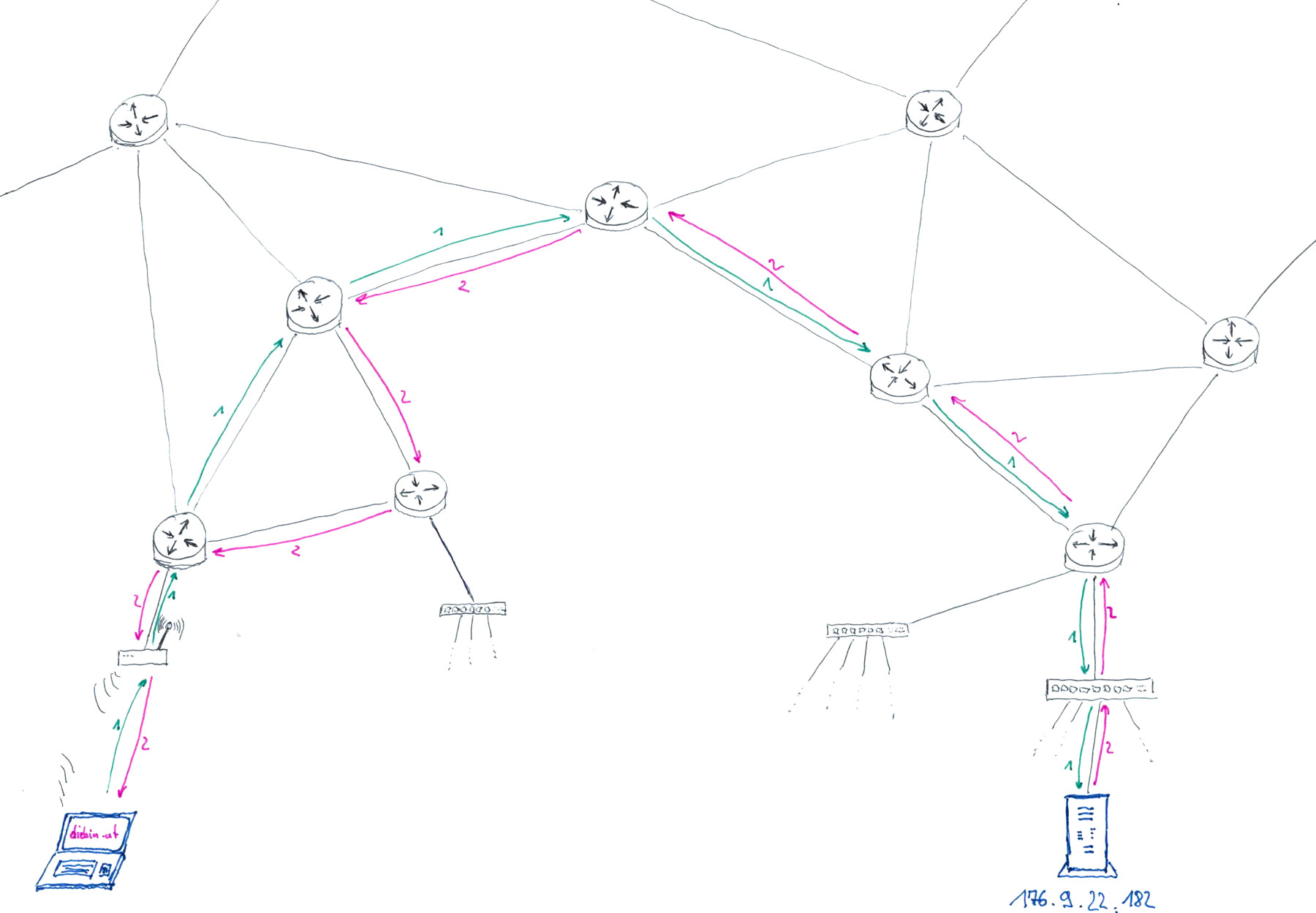
What happens when I visit a website?
excerpt from Sending Passwords on Postcards, recording available on YouTube
- I enter https://diebin.at into my browser and hit return
- My browser asks the DNS server "What's the IP address of diebin.at?" and waits for a response - "Hey there, it's: 176.9.22.182!".
- My browser sends a first HTTP request packet through the internet to the IP address 176.9.22.182
-
The webserver running on 176.9.22.182 receives the request and sends the website of "diebin.at" as a HTTP response.
(one or more response packets are sent, depending on the size of the webservers reply) - My computers receives all the packets, assembles them according to TCP/IP protocol, and hands them to my webbrowser
- My browser shows me the response in the form of a website
wait, wait! is that all?
- Imagine this line in your HTML page, that the web server just sent us:
<img src="chockie.png" alt="Picture of a chocolate cookie" /> - My browser requests all the images used in the HTML page that was just loaded
- My browser requests all the CSS files that are used to style my HTML page
- My browser requests all the JS files that are used to make my HTML page nicely interactive
- ... and potentially lots more of (auto)magic stuff ✨🪄✨
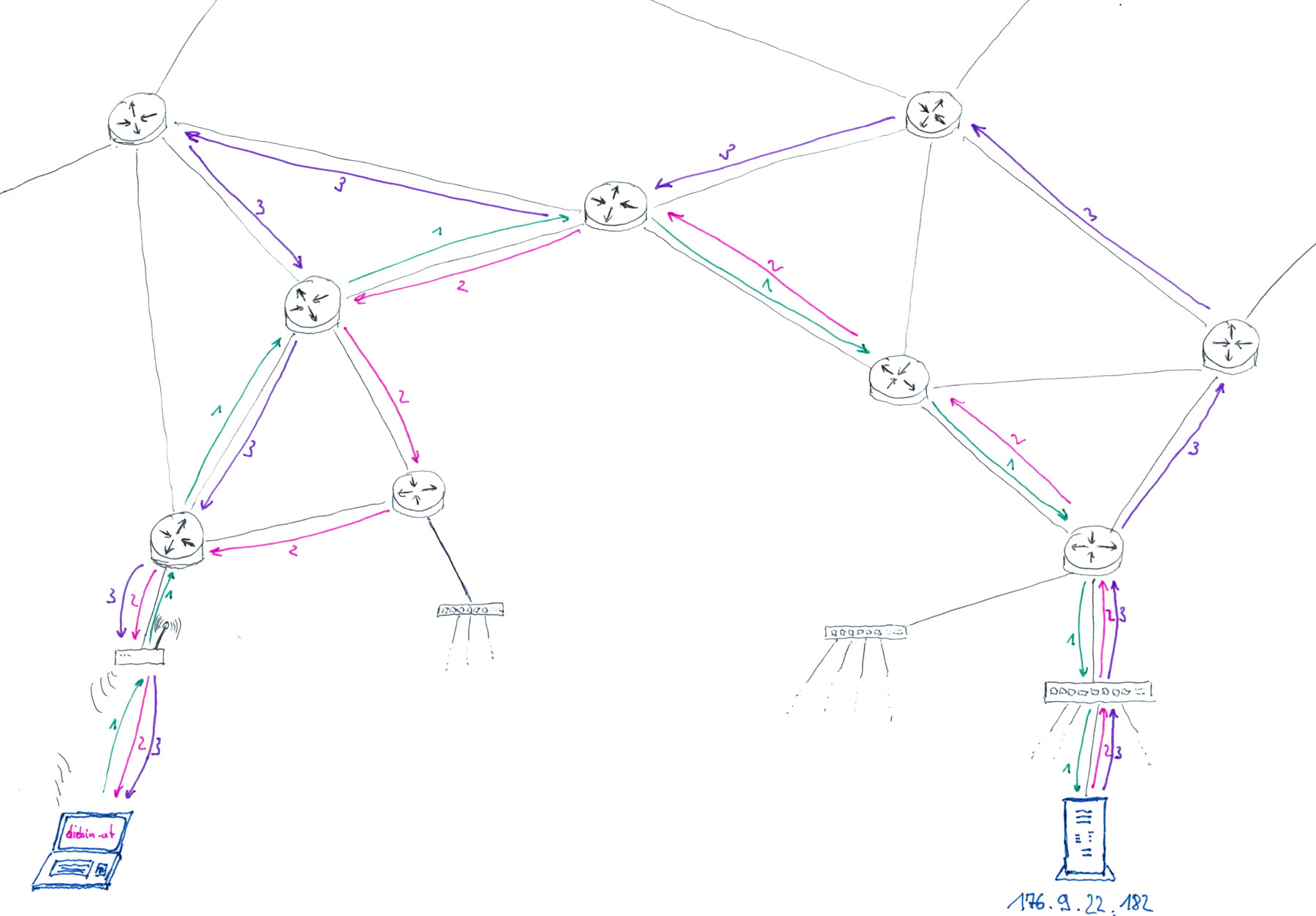
web sites vs.
web applications
- mostly static hyperlinked content vs. highly interactive programs accessible through a web browser

(Source: https://de.wikipedia.org/wiki/Datei:Webanwendung_client_server_01.png , under CC BY-SA 3.0 license)
web hacking quickstart reference
on the web app sec course page there is a link to
The Browser Environment
developer tools
hit Ctrl+Shift+I(Firefox)
or Ctrl+Shift+J(Chromium)
or right-click and "Inspect"
Inspector
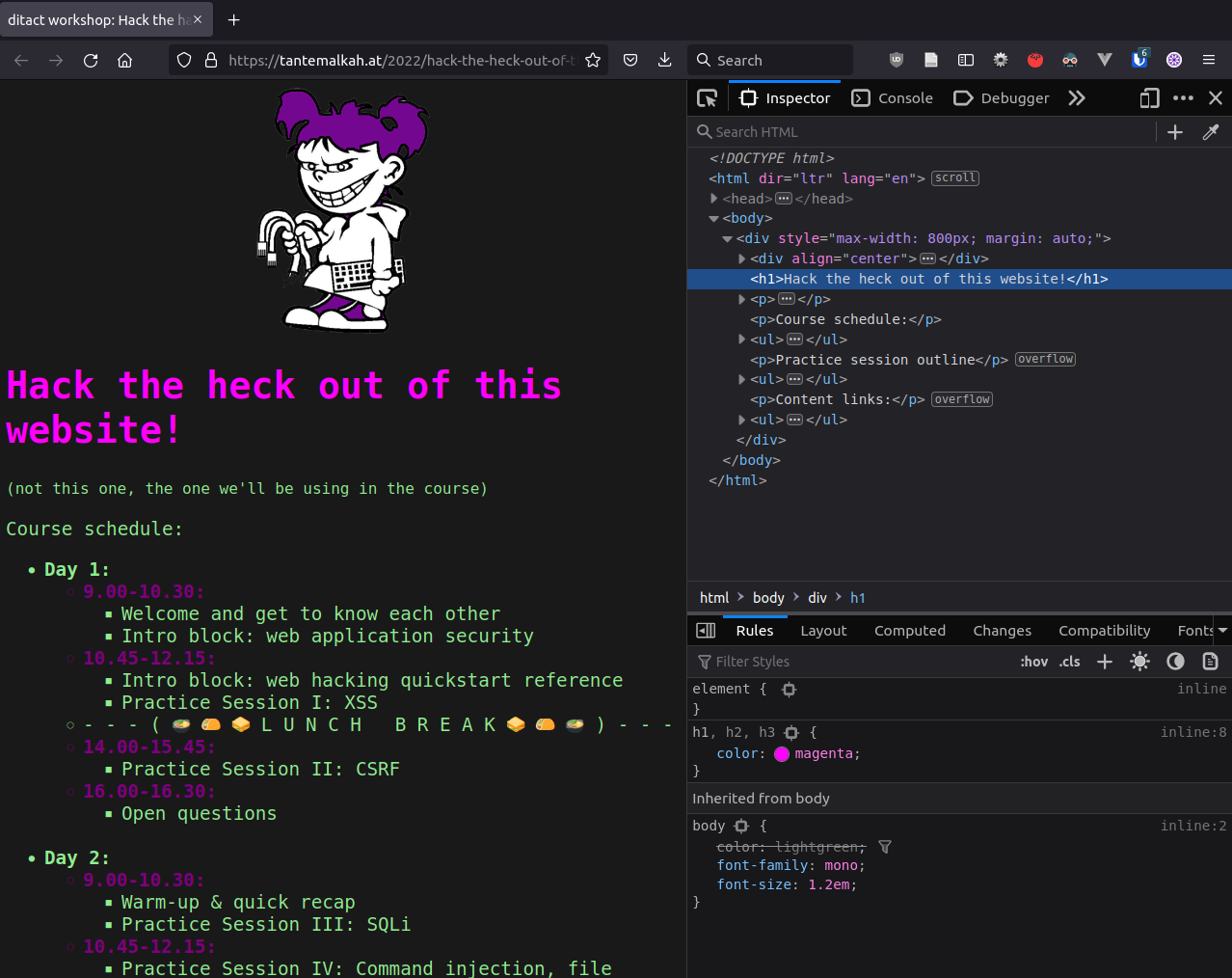
Console
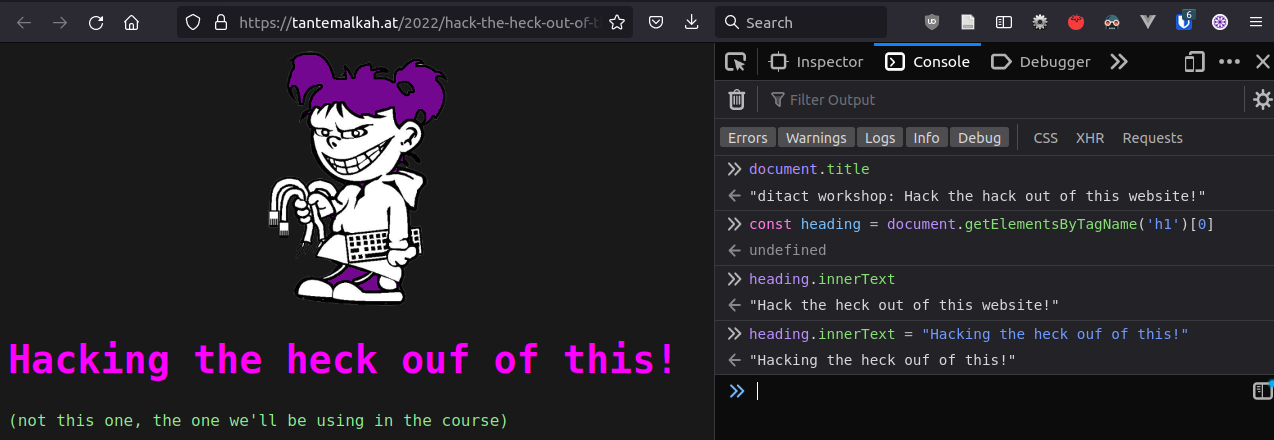
Network
Storage
Some useful JS functions
try it out!
... right there in the browser console
alert("hey there!")
// or even simpler:
alert(1)
document.body
document.getElementById("try-it-out")
window.location
// and then let's change it
window.location = 'https://tantemalkah.at'
// this can be quite useful, but not very versatile in the console
// because everything you set here is gone after a reload
window.onload
Clickable commands in HTML tags
Using the onclick property of HTML tags
<p onclick="alert('are you sure you should have clicked that?')">...some text here...</p>
Here is an example.
Wouldn't you just want to click on this nice paragraph here?
It seems so deliciously clickable. With a bit of extra CSS crust.
A bit of border around it, color and changing the mouse cursor.
All just to make it more clickable.
Come on, click this shiny big button.
XSS
Cross-Site Scripting
on the web app sec course page there is a link to
an intro to XSS
Interlude:
VMs & Containers
a practical kick-starter
with a very brief theoretical intro
(hardware) virtualisation
creating a virtual machine (with virtual hardware) in which an OS can be run as if it would be installed on its own computer
the virtualisation host contains some form of virtualisation software (ideally hardware-assisted) that allows us to create virtual machines on which guest operating systems can be run
containerisation
creating multiple isolated process environments that can run on the same operating system
a specific approach to OS-level virtualisation

Source: kubernetes.io, CC-BY 4.0
if you really want to know:
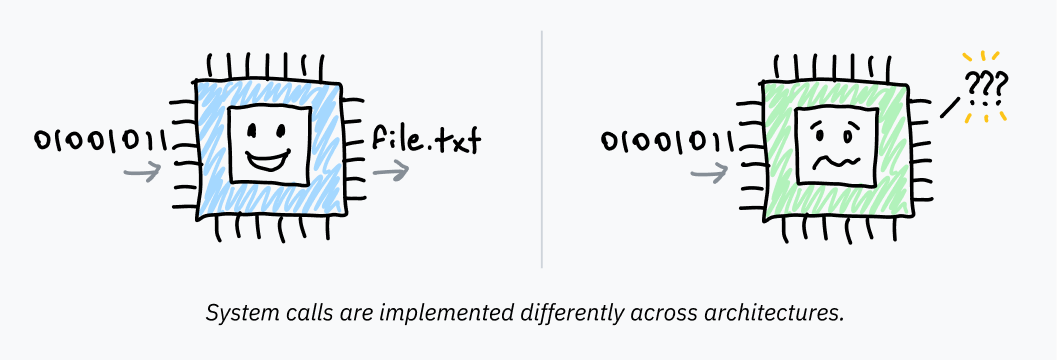
cpu.land
A technical explainer of how your computer runs programs, from start to finish.
By @kognise[Lexi Mattick (she/her)].
Under MIT license. Picture above is on https://cpu.land/the-basics
Now for the practical part...
- Spinning up a virtual Kali box
- Installing docker
- Starting a basic container
- Spinning up DVWA with Docker
Install docker (in your Kali VM)
# Add Docker's official GPG key:
sudo apt-get update
sudo apt-get install ca-certificates curl
sudo install -m 0755 -d /etc/apt/keyrings
sudo curl -fsSL https://download.docker.com/linux/debian/gpg -o /etc/apt/keyrings/docker.asc
sudo chmod a+r /etc/apt/keyrings/docker.asc
# Add the repository to Apt sources:
echo \
"deb [arch=amd64 signed-by=/etc/apt/keyrings/docker.asc] https://download.docker.com/linux/debian trixie stable" | \
sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
sudo apt update
# Now install Docker
sudo apt install docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin
Starting basic containers
# just testing if everything works
docker run --rm hello-world
# starting a shell inside a basic Alpine Linux container
docker run --rm -it alpine sh

Spinning up a DVWA
Remmeber: this is a Damn Vulnerable Web Application
# get the compose file from the DVWA repo
mkdir dvwa && cd dvwa
wget https://raw.githubusercontent.com/digininja/DVWA/refs/heads/master/compose.yml
# spin up the containers
sudo docker compose up
# visit http://localhost:4280 (with a browser in the kali VM)
# hit CTRL-C when you want to stop them again
# alternatively spin up in background (daemon mode)
sudo docker compose up -d
# check out what is running
docker ps
# stop them again (and clean up)
sudo docker compose down
🍲🌮🥪 lunch break 🥪🌮🍲
13:00 — 14:00
SQLi
SQL injection
on the web app sec course page there is a link to
an intro to SQLi
Command injection, file inclusion, file upload
on the web app sec course page there is a link to
 (Source: https://commons.wikimedia.org/wiki/File:Http_request_telnet_ubuntu.png , under public domain)
(Source: https://commons.wikimedia.org/wiki/File:Http_request_telnet_ubuntu.png , under public domain)