Ethical Hacking
FH Salzburg
Sommersemester 202x (rolling release)
This is the waiting queue slide. Hit space or right arrow key to jump to cover slide.
Port scanning & enumeration
FH Salzburg, Sommersemester 202x (rolling release)

jackie / Andrea Ida Malkah Klaura <jackie@tantemalkah.at>
https://tantemalkah.at/ethical-hacking
🌒⇆🌖 Use page style to switch to light mode.Overview
TODOA word about protocols

(Source: https://xkcd.com/927/ , under CC BY-NC 2.5 license)
TCP/IP
All the protcols you need
- We mostly need to know about layer 4 protcols: TCP and UDP
- IP and ICMP are generally good to know too
- The goal of port scanning: find out where something is listening
- The goal of service enumeration: find out what is listening (=which apps are running, and whether they are vulnerable)
TCP/IP Layers & Routing

Source: Wikpedia [en]: Internet protocol suite (2025-05-30)
CC BY-SA 3.0, Kbrose
Full details @ Wikimedia Commons: File:IP stack connections.drawio.png
TCP/IP Layers data encapsulation
 Source: Wikpedia [en]: Internet protocol suite (2025-05-30)
Source: Wikpedia [en]: Internet protocol suite (2025-05-30)CC BY-SA 3.0, Cburnett, Kbrose
Full details @ Wikimedia Commons: File:UDP encapsulation.svg
TCP header
 Source: Wikpedia [de]: Transmission Control Protocol (2025-05-30)
Source: Wikpedia [de]: Transmission Control Protocol (2025-05-30)CC BY-SA 3.0, Appaloosa
Full details @ Wikimedia Commons: File:TCP Header.svg
TCP and the 3-way handshake
 Source: Wikpedia [de]: Transmission Control Protocol (2025-05-30)
Source: Wikpedia [de]: Transmission Control Protocol (2025-05-30)CC BY-SA 3.0, Appaloosa
Full details @ Wikimedia Commons: File:Tcp-handshake.svg
Internetprotokoll-Übersicht
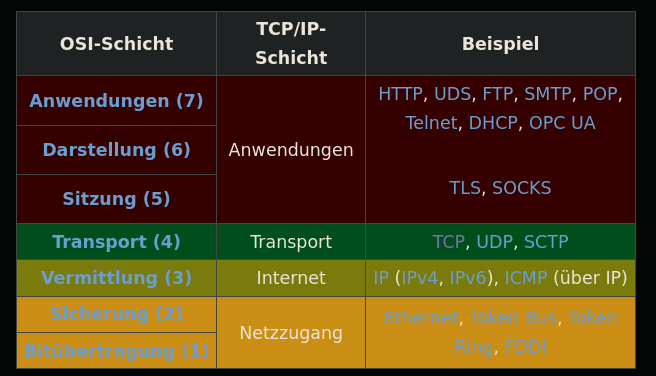 Screenshot, Quelle: Wikipedia [de]: Internetprotokollfamilie (2025-05-30)
Screenshot, Quelle: Wikipedia [de]: Internetprotokollfamilie (2025-05-30)
Demo / mini exercise
- Spin up wireshark (e.g. in your Kali box) and start capturing on your main network device
- Open a terminal next to it
- Make a simple HTTP GET request to a site of your choice
- e.g.:
curl -v fh-salzburg.ac.at
- e.g.:
- practical filters
tcp.dstport == 80ip.addr == 193.170.193.57
Port scanning
legal disclaimers
"When used properly, Nmap helps protect your network from invaders. But when used improperly, Nmap can (in rare cases) get you sued, fired, expelled, jailed, or banned by your ISP. Reduce your risk by reading this legal guide before launching Nmap." (https://nmap.org/book/legal-issues.html, 2025-05-31)
"The best way to avoid controversy when using Nmap is to always secure written authorization from the target network representatives before initiating any scanning." (ibid)
"Port-Scans sind und bleiben nützliche Anwendungen zur Identifizierung von Sicherheitslücken, können aber auch missbräuchlich verwendet werden. Eine Strafbarkeit ist jedoch in den allermeisten Anwendungen nicht gegeben. Jedenfalls dann nicht wenn der Port-Scan ausschließlich seinen systemschützenden Zweck erfüllt." (Reichert & Reichert Datenschutzblog: Ist die Nutzung eines Port-Scans strafbar?, 2025-05-31)
general approach
- detect live hosts on a network
- as soon as we get an answer from a host, we know it is is online
- depending on firewalls and system configs, we need to use different methods
- detect open ports on specific systems
- we just want to know on which ports some service is listening
- we don't care yet, what exactly is listening there
- service enumeration (detect running service versions and vulnerabilites)
- OS detection is usually also part of this
Common tools
- nmap (kind of the industry standard)
- masscan (for high-speed scanning)
- Unicornscan (information gathering and correlation engine)
- hping3 (packet generator & analyzer; author invented the idle scan)
- Mausezahn (Packet generator, not usually used for scanning, but here for the funny name)
broadcast pings
Sometimes you just want to know which devices answer on you local subnet.
In this case you don't need to pull up a battleship like nmap.
You can just send out a broadcast ping and see what answers:
ping -b 10.0.39.255
Not all devices answer to a broadcast ping. But if you just want to see if anything is out there, this might be fine.
nmap
Default scan
- Scans 1000 most common ports on a host (or host range)
- Scan a single host:
nmap 127.0.0.1 - Scan a whole subnet:
nmap 127.0.0.1-255, ornmap 127.0.0.1/24
- Scan a few hosts in a subnet:
nmap 127.0.0.1,2,3,4,6,9, ornmap 127.0.0.1-4,6,9
- Specific IPs can be exlcuded with
--excludeor
--excludefile <filename>options
Using port ranges
nmap -p 1-1024 127.0.0.1nmap -p 1-111,443-631,12345,23456 127.0.0.1- can be combined with ip ranges:
nmap -p 1-111,443-631,12345,23456 127.0.0.1/24 - common ports can be referenced with service name:
nmap -p 1,2,3,ssh,ipp 127.0.0.1 - open indices can be used for ranges:
nmap -p -1024,60000- 127.0.0.1
nmap -p - 127.0.0.1(this scans all 216 (=64Ki) ports)
Host discovery
- We want to scan efficiently: only do extensive port scans on hosts that are up
- Different techniques to see if a host is up:
![]()
- Default:
"If no host discovery options are given, Nmap sends an ICMP echo request, a TCP SYN packet to port 443, a TCP ACK packet to port 80, and an ICMP timestamp request. [...] These defaults are equivalent to the -PE -PS443 -PA80 -PP options." (nmap man page)
- In some cases it is more complicated than that. So please, RTFM!
List scan: -sL
- does not scan anything
- but still performs reverse DNS lookups
- Why use this?
"It is often surprising how much useful information simple hostnames give out." (nmap man page)
No port scan (a.k.a. "ping scan"): -sn
- only do host discovery (uses the default quoted two slides back)
- skip any heavier follow-up scans
- will print all found hosts that are up
- Hint from the nmap man page:
"It allows light reconnaissance of a target network without attracting much attention. Knowing how many hosts are up is more valuable to attackers than the list provided by list scan of every single IP and host name.
Systems administrators often find this option valuable as well. It can easily be used to count available machines on a network or monitor server availability. This is often called a ping sweep, and is more reliable than pinging the broadcast address because many hosts do not reply to broadcast queries."
No ping: -Pn
"By default, Nmap only performs heavy probing such as port scans, version detection, or OS detection against hosts that are found to be up." (nmap man page)
- With this option we turn off host detection completely
- Heavy scanning is performed on all hosts in the given network range
- Can be very time consuming, and we might be generating a lot of unneccesary traffic
- But we can also find hosts, where the RST flag is suppresed (e.g. by a firewall)
TCP SYN Ping: -PS
- A standard SYN packet is sent to a default port (80)
- We can choose different ports, e.g.
-PS22, or-PS22-25,80,113,1050,35000 - Nmap just wants to know whether the scanned host repsonds either with a SYN/ACK or RST. In both cases the host is up.
TCP ACK Ping: -PA
- Similar to SYN Ping, only now nmap just sends a TCP ACK packet
- Alternate ports can be choosen the same way
- A properly set up host should respond with RST in any case.
- Can be used in combination with SYN Ping. See man page for details.
UDP Ping: -PU
- Sends an empty UDP packet to port 40125, which is most likely not in use
- Alternate ports can be chose like in the above cases
- Why this?
"Upon hitting a closed port on the target machine, the UDP probe should elicit an ICMP port unreachable packet in return. This signifies to Nmap that the machine is up and available. [...] The primary advantage of this scan type is that it bypasses firewalls and filters that only screen TCP" (nmap man page)
ARP scan: -PR
- uses ARP requests on local networks (Ethernet, Layer 2) to find active hosts
- much faster than other mechanisms
- used automatically when local network range detected, eg. with
nmap -sn 192.168.100.1/24 - can be turned off with
--disable-arp-pingoption
name resolution
- per default nmap does reverse DNS resolution for active hosts
- can be turned off with
-n - can be turned on for ALL hosts (even inactive ones) with
-R
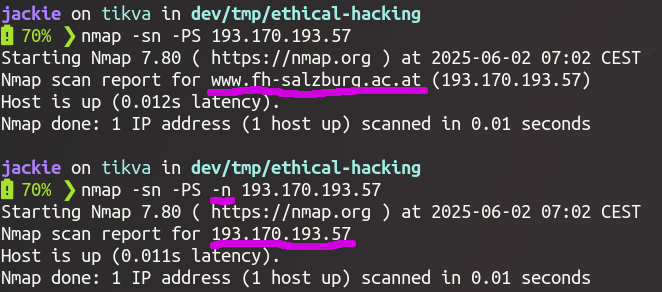 (Not a port scan! Just sends a SYN packet to port 80 to detect if host is alive.)
(Not a port scan! Just sends a SYN packet to port 80 to detect if host is alive.)
scanning techniques

TCP SYN scan: -sS
- default (in privileged mode), and most popular: fast and relatively unobtrusive
- works well with fully TCP-compliant stacks
- also known as half-open scanning, because the 3-way-handshake is not completed
- we just send a
SYNpacket to the destination and way if a SYN/ACK or RST is returned - ports are marked as "filtered", if nothing is returned (assuming the host is up)
TCP connect scan: -sT
- default when SYN scan is not possible (e.g. in unprivileged mode)
- uses the OS-level interface to the TCP/IP stack (as any other app does)
- slower and less stealthy
- establishes a full TCP connection and closes it again, without sending any data
"Truly pathetic services crash when this happens, though that is uncommon." (nmap man page)
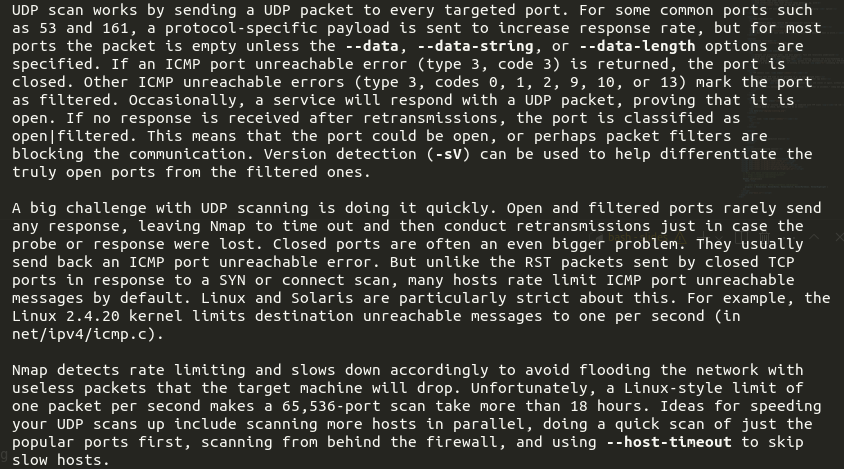
UDP scan: -sU
- scans UDP ports instead of TCP, but can be combined with TYP scans (
-sS -sU) - always good to check, but timing can be an issue, check the man page:
TCP idle scan (a.k.a. zombie scan):
From the man page:
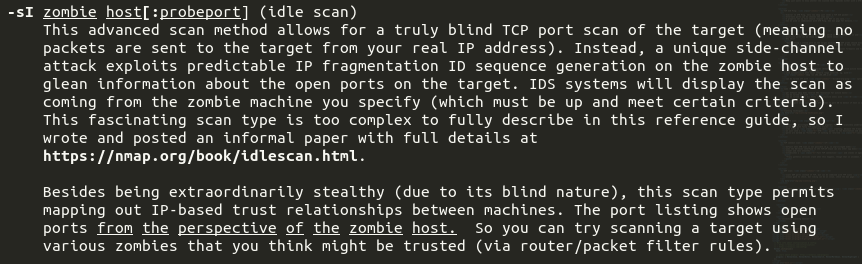
Let's check it out: https://nmap.org/book/idlescan.html
How to find a zombie host
- we need a host, that does IP ID incrementation
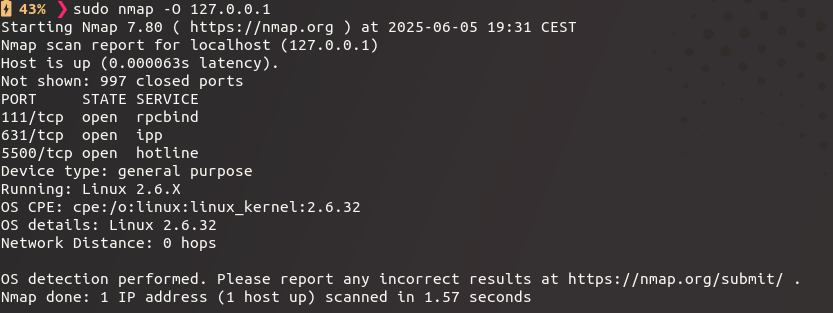
sudo nmap -O -v 192.168.23.42- check for "
IP ID Sequence Generation: Incremental" - also required: no other traffic on the host
- a rarely used dev server?
- a rarely used printer?
- something else that is up but nobody seems to use?
TCP ACK scan: -sA
- not used to scan for open ports, but to map out firewall rules
- only the ACK flag is sent
- from the nmap man page:
- "When scanning unfiltered systems, open and closed ports will both return a RST packet"
- "Ports that don't respond, or send certain ICMP error messages back (type 3, code 0, 1, 2, 3, 9, 10, or 13), are labeled filtered"
IP protocol scan: -sO
"IP protocol scan allows you to determine which IP protocols (TCP, ICMP, IGMP, etc.) are supported by target machines. This isn't technically a port scan, since it cycles through IP protocol numbers rather than TCP or UDP port numbers." (nmap man page)
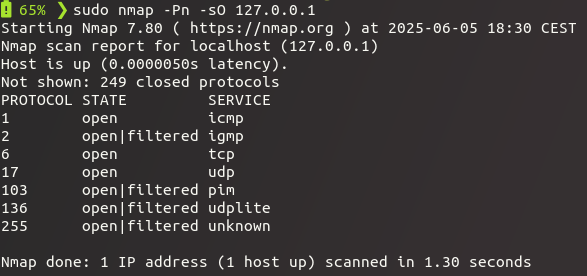
- the
-poption can be used to select protocols to scan for
other scans
- FIN, Xmas und Null scans (-sF, -sX, -sN)
- in RFC-conformant TCP implementations, every package without a SYN, RST or ACK flag leads to a RST response on closed ports, or no answer on open ports
- FIN scan only sets the FIN flag
- Xmas scan sets FIN, PSH, and URG flags
- Null scan does not set any flags (TCP flag header: 0)
- where useful to circumvent firewalls in the olden days
Output formats
- When we scan a lot of systems, we want more structured output, to process and filter it after the scan has completed
- We can redirect the output to a file in three different formats:
-oN: like the default output to the terminal-oX: in an XML format-oG: in agrepable format- You can also use
-oAto get all three
service enumeration
- once we know which ports are open...
- ... we want to know more:
- what service is actually running?
- which application is listening there?
- which version of the application is in use?
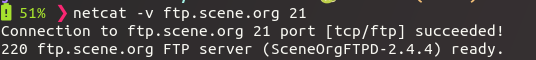
Banner grabbing
- many services provide a banner upon connection
- in default settings these often contain application and version infos
- not always successful and reliable, but can give us some quick first insights
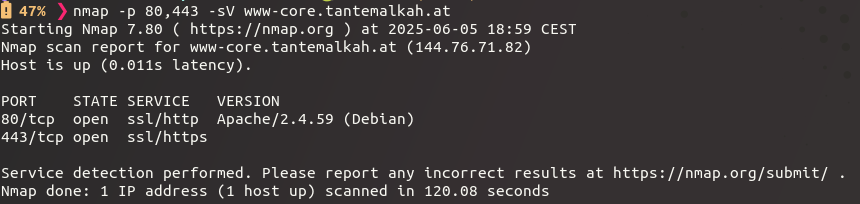
Service & version detection
- if banners are not available, or changed, we can send in some probes with nmap
- nmap tries to correlate the fingerprint of the probed port with its service database
OS fingerprinting -O
- every TCP/IP stack is implemented differently and use different defaults
- by testing different responses (ideally with many ports open), we can fingerprint this behaviour
- and compare these fingerprints with patterns in OS fingerprint database
Convenience vs. stealthiness
- There is an
-Aoption:
"Enable OS detection, version detection, script scanning, and traceroute" - Timing templates
-T0(very slow) to-T5(very fast). The templates even have names:
-T paranoid|sneaky|polite|normal|aggressive|insane
firewall & detection evasion
- general ways to evade a FW or IDS (Intrusion Detection System)
- timing
- source port
- fragmentation
- spoofing
- cloaking
timing
- reduce the scanning traffic, so that it will not look suspicious in the logs / blend in with the rest of the traffic
- see timing templates listed before
source port
- FWs somtimes only allow traffic from defined source ports (e.g. 53 for DNS, or 68 for DHCP)
- we can use
--source-port 53to send all scanning requests from this port - a default scanning packet is typically much smaller than packets for these protocols
- this can be detected by FWs
- we can use
--data-length 1350to increase our packet size
fragmentation
- not really useful anymore with modern FWs/IDSs
- does not work for connect scan and version detection
- nmap option:
-f - packets will be fragmented into multiple fragments (in the hope that a FW might not detect the whole thing)
spoofing
- we spoof our source IP address
- but how do we get back a response then
- remember the zombie/idle scan?
-sI
cloaking
- idea: create a lot of noise at the target, so that we can stay undetected
- beside our own SYN scan packet we generate a lot of other packets with spoofed IP addresses
-D RND:10creates 10 additional packets with random IPs- better: use only IPs as decoys which are currently up
-D decoy1[,decoy2][,ME][,...]
hiding among 10 rando strangers
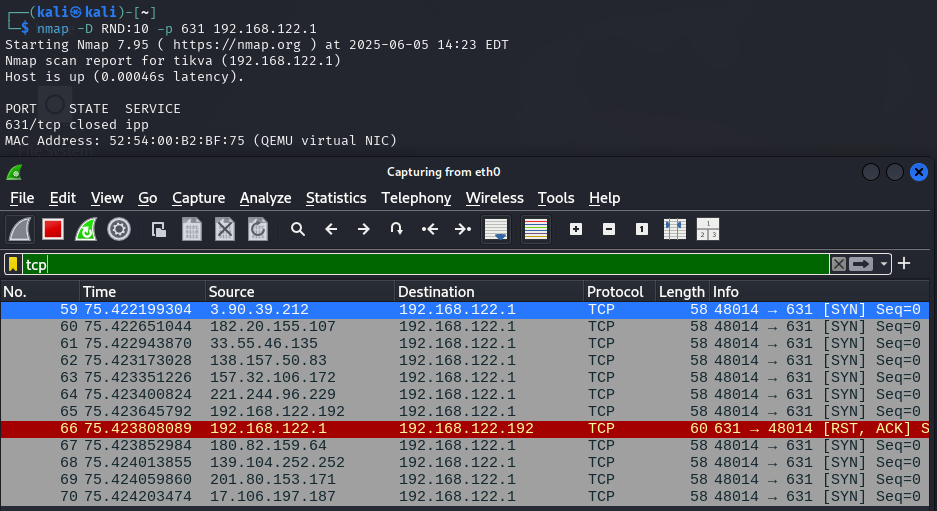
hiding between fh-salzburg.ac.at and dieangewandte.at
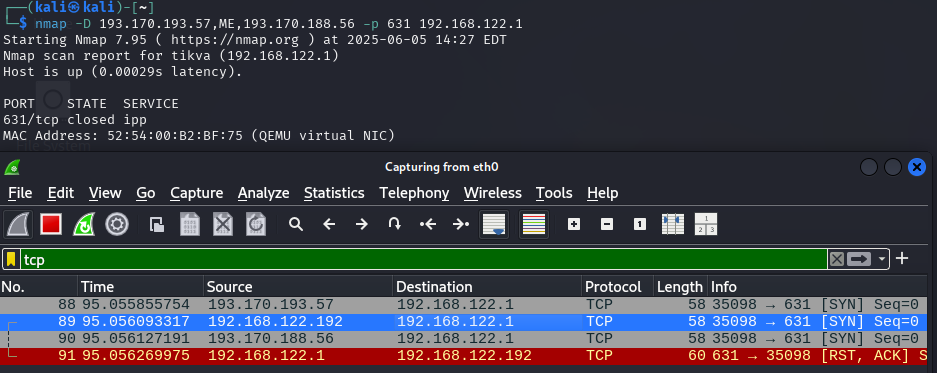
collective scanning session
- first we scan ourselves
- then we scan each other (everyone who accepts)
- and we document all our findings
- coordinated through a Cryptpad, linked in Moodle
