Ethical Hacking
FH Salzburg
Sommersemester 202x (rolling release)
This is the waiting queue slide. Hit space or right arrow key to jump to cover slide.
Web Application Security
FH Salzburg, Sommersemester 202x (rolling release)

jackie / Andrea Ida Malkah Klaura <jackie@tantemalkah.at>
https://tantemalkah.at/ethical-hacking
🌒⇆🌖 Use page style to switch to light mode.Outline
- some security bascis
- web applications
- DWAST (Dynamic Web Application Security Testing a.k.a. ethical web hacking)
- two common vulnerabilities
- a few stats & takeaways
- web hacking quickstart reference
These are excerpts from the
Hack the heck out of this website!
course, originally designed for the
ditact (Women's IT summer academy in Salzburg)
in 2022, together with Melanie Hosinner.
Another ditact course edition coming up this year: 1. & 2. September
some security basics

(Source: https://xkcd.com/538/ , under CC BY-NC 2.5 license)
Key goals in infosec (the CIA triad)
Quotes from Wikipedia [EN]: Information security (section on "Security Goals")
- Confidentiality
- a property of an information system that ensures that users can always only get those informations from the system for which they are authorized to read them
- Integrity
- a property of an information system that ensures that data can be changed only by users who are authorized to do so. Or, in a slightly different framing: the property of a system "assuring the accuracy and completeness of data over its entire lifecycle" (ibid)
- Availability
- a property (or the degree thereof) that an information system is providing functions whenever it is supposed to provide those functions, or in other words: that "the information must be available when it is needed" (ibid)
Access control
- Identification
-
a process of claiming that someone is who they say they are;
e.g. "I am Janoe Doe" ... and here is my ID Card/Password/Token/*
-
a process of claiming that someone is who they say they are;
- Authentication
-
a process of actually verifying that the identification is valid
- by something you know: e.g. a password or passphrase, a PIN or some other code, an answer to a question, …
- by something you have: e.g. a token, an ID card, an RFID chip, …
- by something you are: e.g. finger print, the scan of your retina, …
- 2FA (2 factor authentication) or MFA (multi-factor authentication): use more than one property, from different catagories
-
a process of actually verifying that the identification is valid
- Authorization
- a process to check whether a specific user is allowed to execute a specific action (e.g. read a document, upload a file, change an existing file, send a message, …)
What to look out for
- Vulnerability
- "A vulnerability is a hole or a weakness in the application, which can be a design flaw or an implementation bug, that allows an attacker to cause harm to the stakeholders of an application." (OWASP: Vulnerabilities)
- Exploit
- "a piece of software, a chunk of data, or a sequence of commands that takes advantage of a bug or vulnerability to cause unintended or unanticipated behavior" (Wikipedia [EN]: Exploit (computer security))
- Zero Day (Exploit) (don't keep it to yourself 👿)
- An exploit that is "unknown to everyone but the people that found and developed them" (ibid)
where do vulnerabilities come from?
- faulty/buggy/insecure code
- because developers do not know how to write secure code
- because developers are working under too much pressure to satisfy deadlines and deliver code
- faulty/insecure use of code
- because administrators do not know how to secure the service
- because documentation is bad and it is unclear how a clean (and secure) setup looks like
- because everyone likes to throw around with the buzzword label DevOps, but in practice there is no systematically engineered process in place to assure the quality and security of complex application systems (this is why there now is also DevSecOps)
- faulty/insecure/missing systematic approach to application development
- no one really cares about security
- management layers are ignorant of the importance of security and do not allocate the appropriate resources
- security is not integrated from the start on (e.g. with a secure development life cylce, short SDLC)
the making of a vulnerability
...just some examples...
- in planning & design desicions:
- trusting the user('s browser)
- using outdated or self-coded encryption algorithms and insecure protocols
- while coding:
- incomplete or missing input validation and output sanitization
- insecure methods and queries to access a database
- parsing user provided files (including configs from admins) without precautions
- hardcoding credentials that are not kept in separate configuration files outside any version control
- at run-time:
- using default configuration snipptes without changing sensitive information (e.g. default passwords)
- debugging mode in production systems
- using TLS (or maybe still SSL) in an insecure way (e.g. to be "backwards compatible")
- not using suggested security features, because they are not needed for the app to be functional, but they would require more time to set up and maintain and add complexity
Remember: There is no "100% secure"!
- information security is not a specific state you can reach in any context
- it is rather a chance/probability that you can increase by appropriate measures
web servers & web applications
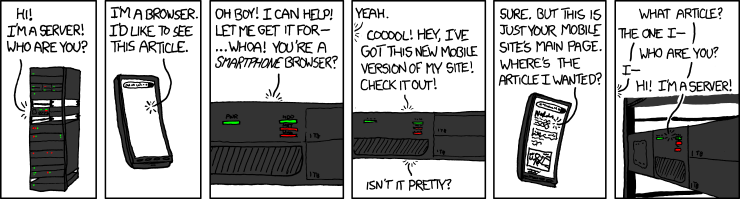
(Source: https://xkcd.com/869/ , under CC BY-NC 2.5 license)
speaking HTTP
- web clients request websites from web servers through HTTP
- a text-based, state-less protocol
- should be used with TLS anywhere -> HTTPS
- the browser does a lot of automagic stuff to display a web-site

(Source: https://commons.wikimedia.org/wiki/File:Http_request_telnet_ubuntu.png , under public domain)
🍪🍪🍪 Cookies 🍪👿🍪
- used for lots of questionable stuff
- but also because HTTP is state-less, e.g. to remember logged in users
-
Part of a server response:
Set-Cookie: sessionToken=abcdef01234567890; Expires=Tue, 31 Aug 2021 12:34:56 GMT Set-Cookie: foo=bar Set-Cookie: chocolate=good Set-Cookie: raisins=evil -
Part of subsequent client requests:
Cookie: sessionToken=abcdef01234567890; foo=bar; chocolate=good; raisins=evil;
What happens when I visit a website?
excerpt from Sending Passwords on Postcards, recording available on YouTube
- I enter https://diebin.at into my browser and hit return
- My browser asks the DNS server "What's the IP address of diebin.at?" and waits for a response - "Hey there, it's: 176.9.22.182!".
- My browser sends a first HTTP request packet through the internet to the IP address 176.9.22.182
-
The webserver running on 176.9.22.182 receives the request and sends the website of "diebin.at" as a HTTP response.
(one or more response packets are sent, depending on the size of the webservers reply) - My computers receives all the packets, assembles them according to TCP/IP protocol, and hands them to my webbrowser
- My browser shows me the response in the form of a website
wait, wait! is that all?
- My browser requests all the images used in the HTML page that was just loaded
- My browser requests all the CSS files that are used to style my HTML page
- My browser requests all the JS files that are used to make my HTML page nicely interactive
- ... and potentially lots more of (auto)magic stuff ✨🪄✨
Short demo: accessing diebin.at with httpie vs. Firefox
web sites vs. web applications
- mostly static hyperlinked content vs. highly interactive programme accessible through a web browser

(Source: https://de.wikipedia.org/wiki/Datei:Webanwendung_client_server_01.png , under CC BY-SA 3.0 license)
With a bit more nuance here: https://hackmd.io/@jackie/Hthootw-Intro
Web application security testing

(Source: https://xkcd.com/2176/ , under CC BY-NC 2.5 license)
Application Security Testing
Two major categories on how to test for weaknesses and vulnerabilities:
- SAST: short for Static Application Security Testing, which means looking at an applications source code to check it for security issues (either manually in a code review or audit, or by automated tools)
- DAST: short for Dynamic Application Security Testing, which means checking an application for security issues while it is running. There are also tools to do this, but a prominent example of DAST is offensive security testing a.k.a. pentesting, where security specialists try to hack a running application, to find security issues that should then be fixed by the developers.
What we do: DWAST ... dynamic web app security testing ... a.k.a. ethical web hacking
General approach for the exercises
- Understand what the page is doing
- Understand how it is doing that
- Analyse what can be modified
- Try to modify stuff to provoke unexpected/unintended responses
- Create your payload / modified request to exploit the vulnerability
Note: if code is available, do look at it - white box testing is more common than black box testing
two common vulnerabilities
Cross Site Scripting (XSS)
- tricking the web app to include JS code into the HTML output
- imagine a normal greeting:
Hello Mafalda, how are you?
- What if the user did not just type "Mafalda" when asked for their name?
Hello Mafalda<script>alert('eeeevil!')</script>, how are you?
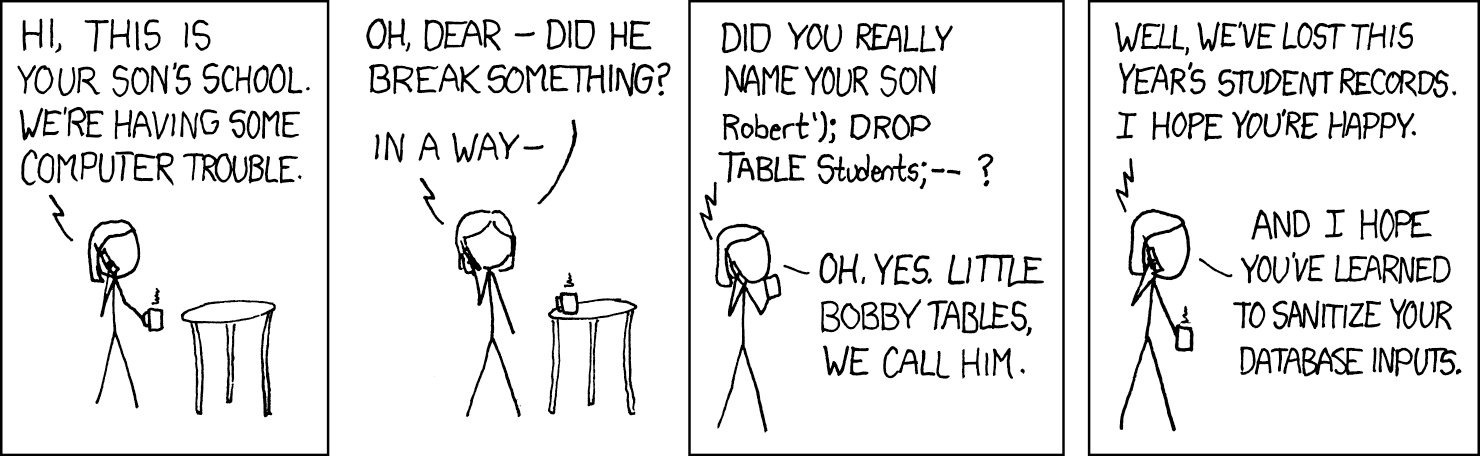
SQL injection (SQLi)
- tricking the web server to include SQL code in a database query
- imagine a query for a user that just has logged in:
SELECT * FROM users WHERE id = "mafalda"; - What if the user did not just type
mafaldawhen asked for their username? - Let's assume they typed
mafalda" OR 1 = 1; --SELECT * FROM users WHERE id = "mafalda" OR 1 = 1; --"; -
Or in the style of Li'l Bobby Tables:
mafalda"; DROP TABLE users; --
... in action
- spinning up DVWA and OWASP Juice Shop with docker
- testing out some (simple) XSS & SQLi
demo.mp4 (~22min, 72MB)
Update 2024-03-10:
The open port mapping I mention in the video is meanwhile
fixed for the OWASP Juice Shop.
I opened an issue,
and they fixed it within a few days. 💜
Update 2024-03-13:
Now also fixed for the DVWA. I created a PR today,
and it was merged within an hour. 💜💜
stats & context
OWASP Top 10
- https://owasp.org/www-project-top-ten/
- THE authoritative survey on vulnerability prevalences
- by the Open Worldwide Application Security Project
- 2017: Injection on place 1, XSS on place 7
- 2021: Injection (including XSS) on place 3
- 2025: "planning to announce the release [...] in the first half of 2025"
Example: WordPress
Source: The Wordfence 2023 State of WordPress Security Report
- Top 5 vulns disclosed in 2023:
- XSS (1963 cases reported)
- CSRF (1098 cases reported)
- Missing Authorization and Authorization bypass (885 cases reported)
- SQLi (279 cases reported)
- Information Disclosure (98 cases reported)
Update 2024 basically the same, just more of it:
2024 Annual WordPress Security Report by Wordfence
Important: most vulns come from plugins, very few in WordPress core
takeaways
for devs
- always validate (user) input
- always sanitize (the final HTML) output
- always use prepared statements or go for ORMs!
- don't do everything from scratch, use frameworks!
- and pleeeeease update them in time!
- I know, I know, there is no 100% in security, but:
if you make exceptions from above rules, you really need to know what you are doing! - nag your higher-ups about secure coding workshops and a proper SDLC
a note on updates
this one also goes out to ops and management
"WordPress has made it significantly easier to keep plugins and themes updated with a user-friendly auto-update mechanism, and regularly pushes updates for critical vulnerabilities even in cases where the user-facing auto-update mechanism is not enabled. Nonetheless, many sites intentionally and fully disable automatic updates, even for critical security issues, which significantly increases their chances of compromise. If your organization has disabled automatic updates to prevent compatibility issues, ensure that you have a process in place to rapidly review security patches and apply them before they can be targeted."The Wordfence 2023 State of WordPress Security Report, p.19
references
- Hack the heck out of this website! (course docs by Melanie & me)
- Tanya Janca: SheHacksPurple YouTube channel
- Sonya Moisset: Open Source Software Security Handbook
- Megan Kaczanowski:
events
- ditact women's IT studies - 25. Aug. - 5. Sep. 2025 (including my web app sec course)